Just In Time access to Azure VMs
A brute-force attack is a cryptanalytic attack that can, in theory, be used to attempt to decrypt any encrypted data (except for data encrypted in an information-theoretically secure manner). Such an attack might be used when it is not possible to take advantage of other weaknesses in an encryption system (if any exist) that would make the task easier. (source: Wikipedia)
Brute force attacks commonly target management ports (22 for SSH, 3389 for RDP etc.) as a means to gain access to Compute VMs. If the attack is successful then the attacker gets access to your environment.
Microsoft Azure has plenty defense mechanism against attacks of that type. The first line of defense for an Azure VM is the Just In Time (JIT) access where we can enable on-demande access to the VMs.
JIT explained
Just-in-Time (JIT) access is a fundamental security practice where the privilege granted to access applications or systems is limited to predetermined periods of time, on an as-needed basis. This helps to minimize the risk of standing privileges that attackers or malicious insiders can readily exploit. (source: Thycotic)
Azure Security Center provides several threat prevention mechanisms to help you reduce surface areas susceptible to attack. One of those mechanisms is Just-in-Time (JIT) VM Access. JIT focuses on the ports that we open in order to access a Virtual Machine where in many cases remain open till manually closed. Those management ports should not need to be open at all times.
By enabling JIT for our VMs, you create a policy that protects those ports by defining how long they will remain open as also allow approved IPs to access those ports and thus that Virtual Machine. The policy helps you stay in control of what users can do when they request access. Requests are logged in the Azure Activity Log, where monitor and audit access can be of help. The policy will also helps quickly identify existing virtual machines that have JIT enabled and virtual machines where JIT is recommended.
Microsoft Defender for Cloud (previously named Azure Security Center) can provide information for VMs that have not enable the JIT access.
Enabling JIT access
- Launch an Azure VM.
- Go to your running VM. Under Settings >> Configuration section
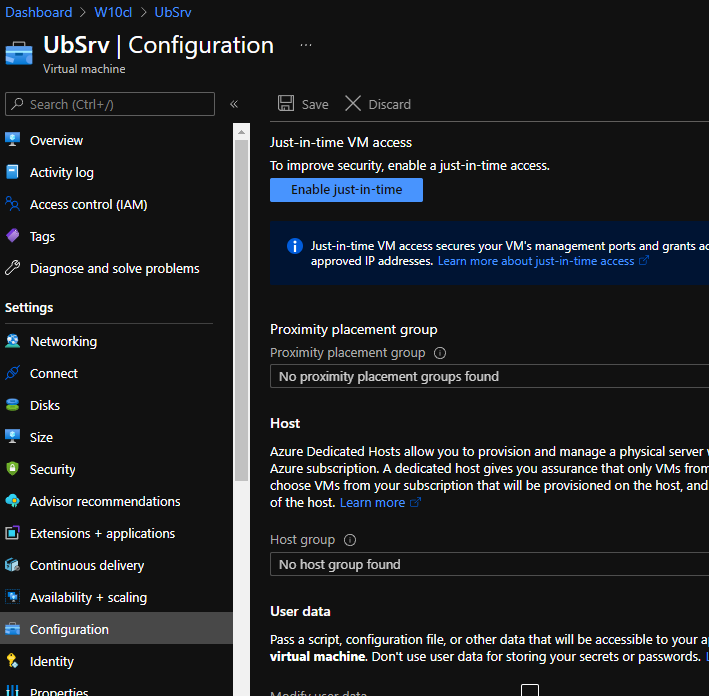
- Click on “Enable just-in-time” button.
- Go back to Microsoft Defender for Cloud blade in Azure Portal. select “Enhance your threat protection capabilities” under Enhance your threat protection capabilities section
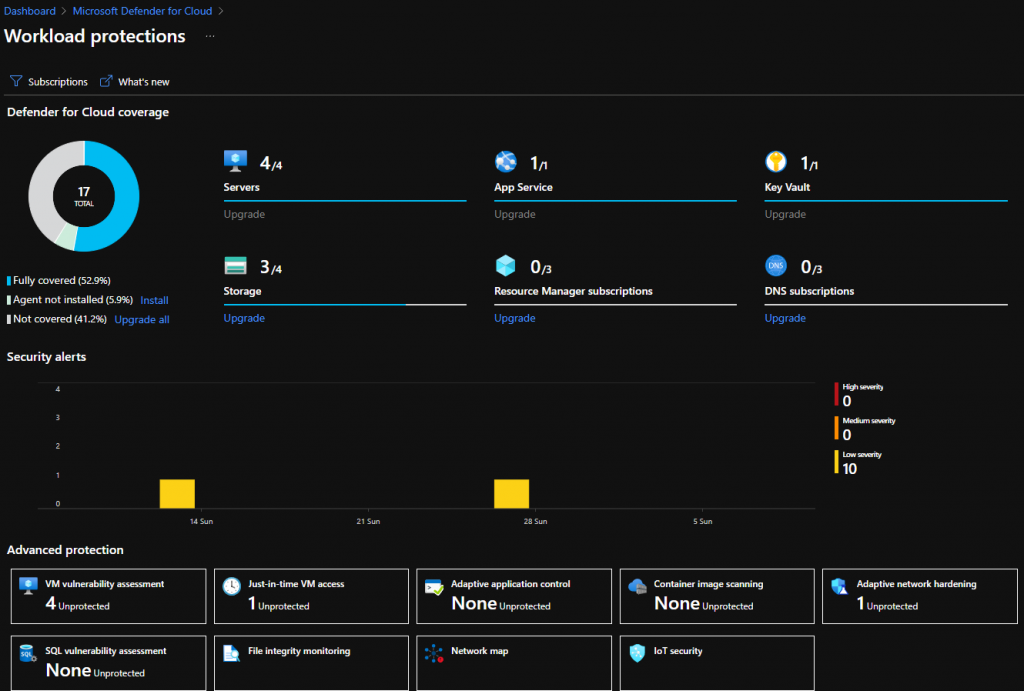
- Click on ““Just in time VM access”
- JIT configuration and monitor of the VMs that have or need JIT can be done in that dashboard and any requests for JIT that have been made can be also seen there. This is another point that you can choose to request access via JIT.
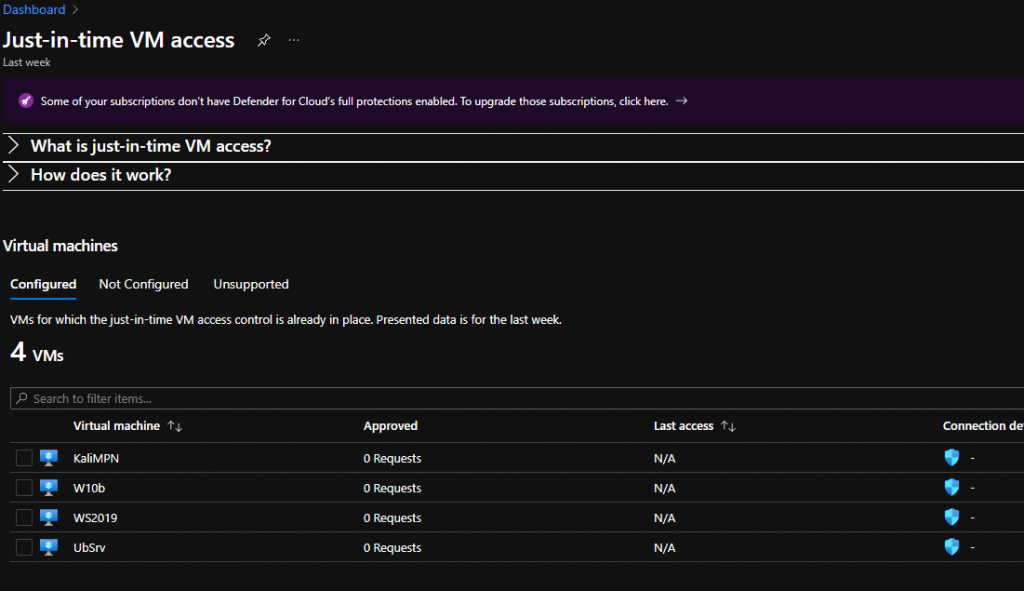
- Choose any VM and the “Request Access” button will enable on the right.
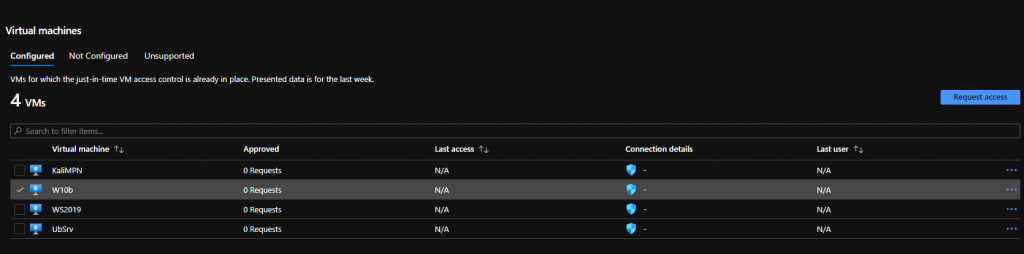
- Click on Request Access
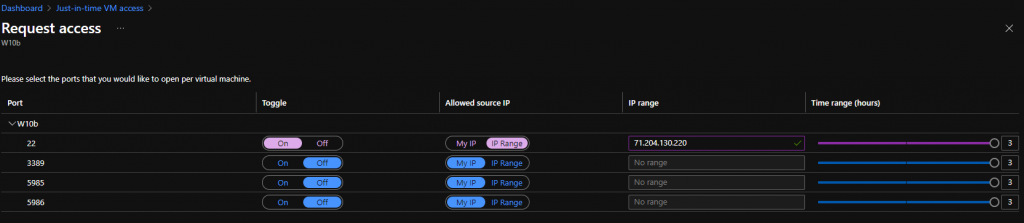
- Toggle the On/Off option and choose the My IP or IP Range. In order to continue, you will find below a space where you have the chance to provide a Justification and then click on Open Ports.
- After this change you can only SSH to this VM from the source IP. Any other source IPs will get denied access. When the agreed time has expired, JIT VM Access will automatically remove the allowed rule and re-lock down the environment.
Conclusion
Amongst many security solutions that Microsoft provides, Just-in-Time VM Access reduces your surface area exposed to RDP/SSH brute-force attack. This feature is available in the standard pricing tier of Azure Security Center.
